Imagine this: you’re on the run from a dangerous criminal, desperately trying to blend in and disappear. But even in a bustling city, every move you make leaves a digital footprint. This footprint, accessible through interconnected law enforcement databases, could be the key to your capture. This is the reality of the modern criminal justice system, where information, shared through systems like TLETS/NLETS, helps law enforcement officers track suspects, recover evidence, and ensure public safety.
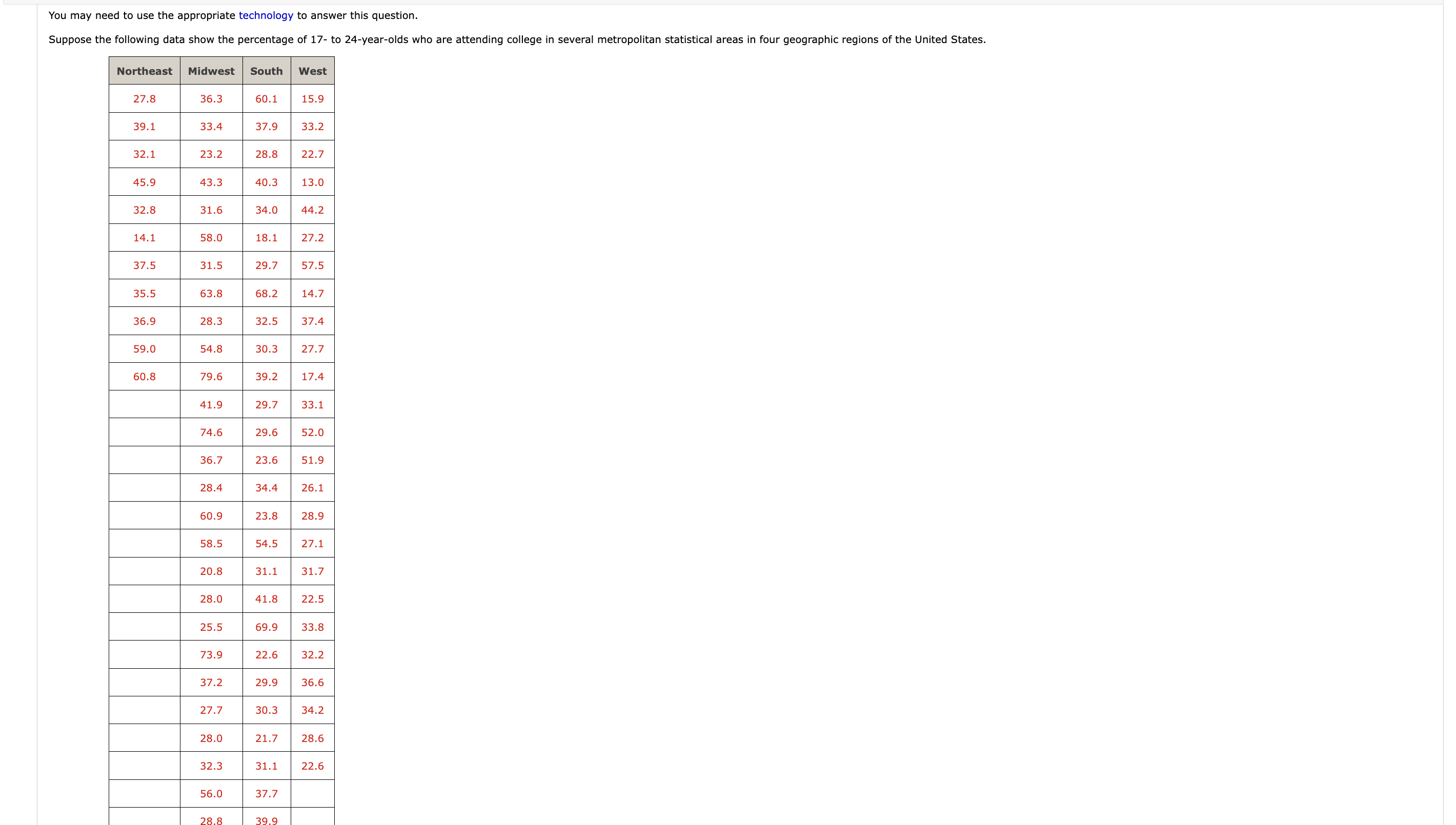
Image: www.chegg.com
The interconnectedness of these systems is crucial, but it also raises questions about data privacy and the potential for misuse. This article dives deep into the world of TCIC/NCIC information obtained through TLETS/NLETS, exploring who can access this sensitive data and the ethical considerations surrounding its use.
Understanding TCIC/NCIC Information & TLETS/NLETS
What is TCIC/NCIC?
The **National Crime Information Center (NCIC)** is a comprehensive database maintained by the Federal Bureau of Investigation (FBI). It houses records on individuals wanted for crimes, missing persons, stolen property, and more. States have their own corresponding databases, like the **Texas Crime Information Center (TCIC)**, which share information with NCIC.
What are TLETS/NLETS?
The **Telecommunications Law Enforcement Information Network (TLETS)** in Texas and the **National Law Enforcement Telecommunications System (NLETS)** are communication networks that allow authorized law enforcement agencies to access and share information across state lines. They act as the digital highway connecting local, state, and federal law enforcement institutions, facilitating rapid data exchange and collaboration.
Image: www.chegg.com
Who Can Access TCIC/NCIC Information Over TLETS/NLETS?
Access to TCIC/NCIC information is strictly regulated and limited to authorized users. These users must undergo rigorous background checks, training, and ongoing oversight to ensure the integrity of the data and prevent misuse.
Authorized users typically include:
- Law Enforcement Officers: State, county, and local police officers, sheriff’s deputies, and federal law enforcement agents are authorized to access TCIC/NCIC information as part of their official duties.
- Prosecutors: Prosecutors use TCIC/NCIC data to gather evidence for criminal cases and to track the movements of individuals under their jurisdiction.
- Judges and Court Officials: Judges and court personnel can access TCIC/NCIC information when making decisions related to bail, sentencing, and other judicial matters.
- Correctional Officers: Correctional officers use TCIC/NCI information to manage inmates, confirm identities, and track escapees.
- Other Authorized Personnel: This might include probation and parole officers, background check agencies, and certain government agencies involved in investigations or security measures.
Individuals and organizations outside law enforcement generally do not have direct access to TCIC/NCIC information. However, in some limited instances, individuals can request background checks or information retrieval through authorized agencies, like law enforcement departments or licensing boards.
Ethical Considerations & Data Privacy
While the use of TCIC/NCIC information is crucial for law enforcement, it’s essential to recognize the potential for misuse and the impact on individual privacy.
Privacy Concerns
The vast amount of personal data collected in TCIC/NCIC raises significant privacy concerns. Improper access or use of this information could lead to identity theft, discrimination, or even wrongful arrests.
Potential for Misuse
The potential for misuse of TCIC/NCI data exists, especially when access controls are not enforced or when individuals abuse their authority. For example, law enforcement officers could use information for personal gain or to harass individuals, or data breaches could compromise sensitive information.
Importance of Data Security
Protecting data housed in TCIC/NCIC is paramount. Continuous monitoring, robust security protocols, and ongoing training for authorized users are crucial to prevent data breaches, unauthorized access, and cyberattacks.
Trends and Developments
The use of TCIC/NCIC information and systems like TLETS/NLETS is constantly evolving with technological advancements and changing legal landscapes. Here are some key trends and developments:
- Increased Data Sharing: There’s a growing trend towards information sharing between different law enforcement agencies and countries, expanding the potential reach of TCIC/NCIC data.
- Biometric Data Integration: Databases like TCIC/NCIC are increasingly incorporating biometric data like fingerprints and facial recognition to improve identification accuracy.
- Data Privacy Regulations: Stricter data privacy laws, such as the General Data Protection Regulation (GDPR), are influencing the handling and sharing of personal information, including TCIC/NCIC data.
- Cybersecurity Focus: With increasing cyber threats, law enforcement agencies are prioritizing data security measures to protect TCIC/NCIC information from attacks and unauthorized access.
Tips for Individuals and Law Enforcement
Here are some tips to ensure the responsible use of TCIC/NCIC information and to protect individual privacy:
For Individuals
- Be Aware of Your Rights: Be informed about your privacy rights and how your personal information is collected and used by law enforcement.
- Monitor Your Credit: Regularly check your credit report for any suspicious activity that may indicate identity theft.
- Be Cautious Online: Protect your personal information by being cautious about what you share online and who you interact with.
- Report Concerns: If you believe your personal information has been compromised or misused, report it to the appropriate authorities, such as your local police department.
For Law Enforcement Agencies
- Strict Access Control: Implement rigorous access control measures to restrict access to TCIC/NCIC information to authorized users only.
- Regular Audits: Conduct regular audits to ensure compliance with data security regulations and to identify and correct any potential vulnerabilities.
- Employee Training: Provide ongoing training to law enforcement personnel on the importance of data privacy, ethical data handling, and cybersecurity best practices.
- Transparency and Accountability: Establish transparent policies and procedures for data collection, storage, and use, and hold individuals accountable for any misuse or breaches.
FAQ
Q: How can I Find My Personal Information in TCIC/NCIC?
A: You generally can’t directly access TCIC/NCIC information about yourself. Only authorized law enforcement agencies can access this data.
Q: Can I Request to Have My Information Removed from TCIC/NCIC?
A: In most cases, individuals cannot directly request to have their information removed from TCIC/NCIC. However, if certain information is inaccurate, you can challenge and try to correct it through legal channels.
Q: Are There Data Protection Regulations for TCIC/NCIC Information?
A: Yes, both federal and state laws (like the Freedom of Information Act (FOIA), the Privacy Act, and state privacy laws) govern the access and use of TCIC/NCIC information, as well as data protection regulations.
Tcic/Ncic Information Obtained Over Tlets/Nlets May Be Used By
Conclusion
The exchange of information via systems like TLETS/NLETS and databases like TCIC/NCIC is crucial for effective law enforcement. However, the delicate balance between public safety and individual privacy demands careful consideration and rigorous security measures. Maintaining this balance requires ongoing awareness from individuals and law enforcement agencies to ensure data is used responsibly and ethically.
Are you interested in learning more about the implications of TCIC/NCIC information and data privacy in law enforcement? Share your thoughts below!




